
Back to Blogs
A practical guide to security incident investigations—how businesses find the right footage, build clear timelines, and resolve incidents in minutes instead of days.

When a theft occurs, an employee gets injured, or property is damaged, your business doesn't have a camera problem—you have a clarity problem.
Most organizations today have security cameras covering their facilities. The challenge isn't capturing footage. It's finding the right moments, understanding what actually happened, and presenting clear evidence before memories fade, disputes escalate, or liability windows close.
This guide explains how modern security incident investigations work, why traditional approaches fall short, and how businesses are cutting investigation time from days to minutes without sacrificing accuracy.
A security incident investigation is the process of reviewing available evidence—primarily video footage—to understand what happened during a specific event at your facility. The goal is to establish facts, identify responsible parties, and document findings that can support operational decisions, insurance claims, legal proceedings, or policy changes.
Common security incidents that require investigation include:
Responsibility for conducting these investigations typically falls to operations managers, security teams, IT departments, or senior leadership—often whoever is available when the incident is reported. In smaller organizations, this might be a general manager reviewing footage on their own. In larger operations, it could involve dedicated security personnel coordinating with HR, legal, or risk management teams.
The failure point in most security incident investigations isn't technology—it's workflow. Organizations invest in comprehensive camera coverage, then struggle to extract value when incidents occur.
Here's where the process typically breaks down:
Footage is scattered across disconnected systems. Many businesses operate multiple DVR or NVR systems that don't communicate with each other. An incident that spans your parking lot, entrance, and sales floor might require logging into three separate systems with different interfaces, credentials, and export processes. Multi-location organizations multiply this problem across sites.
There's no timeline to guide the search. When someone reports an incident, they rarely provide precise timestamps. "Around lunchtime yesterday" or "sometime last week" forces investigators to review hours of footage manually, hoping to spot the relevant moments. Without context about what happened before or after the main event, critical evidence gets missed.
Nothing is searchable. Traditional security camera systems capture continuous video but provide no way to search it beyond scrubbing through timelines. You can't search for "person in red shirt" or "vehicle entering loading dock" or "cash register transaction." Every review requires watching footage in real time or fast-forwarding while hoping not to miss the critical seconds.
Manual review creates bottlenecks. Someone has to sit down, review footage, take notes, and piece together what happened. This person becomes a bottleneck. When multiple incidents occur simultaneously—or when the person responsible for reviews is unavailable—investigations stack up. Evidence collection that should take minutes stretches into days.
These delays create cascading problems. Evidence degrades as systems overwrite old footage. Witnesses forget details. Disputes harden into conflicting narratives. Insurance claim deadlines approach. What started as a straightforward incident becomes a liability exposure because you couldn't answer basic questions fast enough.
Understanding how most organizations currently handle security investigations reveals why the process feels so inefficient—and why many incidents never get fully resolved.
Here's the typical workflow:
An incident gets reported. Someone notifies management about a theft, injury, dispute, or damage. The report is often vague: "A customer said they slipped in aisle three this afternoon" or "We're missing two cases of product from the warehouse." The clock starts ticking.
Staff begin manually searching footage. Someone—often whoever is available rather than whoever is trained—logs into the security camera system. They navigate to what they believe is the relevant camera. They guess at timestamps based on the incident report, then start scrubbing through footage looking for the right moment.
Investigators guess at timestamps and locations. Without precise information, they expand the search window. "This afternoon" becomes a three-hour review session. If the incident involved movement between areas, they repeat this process across multiple cameras, trying to track a person or vehicle through your facility.
Relevant clips get exported. Once investigators find something that looks relevant, they export it—often as large video files with proprietary formats. These clips get saved to local drives, emailed, or uploaded to shared folders with inconsistent naming conventions.
Files are shared with stakeholders. The exported footage goes to whoever needs to make a decision: HR for employee incidents, risk management for liability claims, operations for theft investigations, or insurance adjusters for damage claims. Recipients may lack the software to view proprietary video formats, leading to additional conversion steps.
Everyone hopes the story is clear. Without context about what happened before or after the exported clip, stakeholders piece together narratives from partial evidence. Gaps in coverage, missed cameras, or insufficient detail lead to inconclusive findings.
This process is time-intensive, often requiring hours spread across multiple people. It's error-prone, with investigators potentially missing critical footage by focusing on wrong cameras or time windows. And it's entirely reactive—you only discover process problems after an incident has already occurred and the investigation has stalled.
The fundamental limitation isn't effort. People work hard to find answers. The limitation is that traditional security camera footage investigation wasn't designed for rapid incident response. It was designed for continuous recording and occasional playback, not for answering urgent questions with distributed evidence.
A systematic approach to security incident response dramatically improves both speed and accuracy. Here's how effective investigations work:
Before touching any video system, gather basic information about what you're investigating. You need three core elements:
Approximate time. Even rough timestamps help. "Between 2 PM and 4 PM yesterday" is better than "sometime this week." If witnesses can narrow it further—"right after the lunch rush" or "just before closing"—document that. Time is your primary search parameter.
Location. Identify where the incident occurred and which cameras would have coverage. Consider not just the primary location but surrounding areas. A theft might have started in the parking lot before moving to the sales floor. An injury might have been caused by a spill that originated in a different area minutes earlier.
Parties involved. Document who was present, what they were wearing, and any identifying characteristics. For incidents involving customers, note whether they arrived by vehicle and where they parked. For employee incidents, note which staff members were on duty. This information guides your review and helps verify you're tracking the right people.
The goal at this stage isn't certainty—it's establishing reasonable boundaries for your search. Spending five minutes gathering context prevents spending an hour reviewing irrelevant footage.
How you search determines how quickly you find answers. Traditional approaches force you to manually scrub through hours of footage. Modern methods let you search based on what actually matters.
Time-based search remains the foundation, but it should be precise. Rather than manually dragging a timeline scrubber, you should be able to jump directly to specific times across multiple cameras. If an incident occurred at 2:47 PM, you want all relevant cameras synchronized to that moment instantly.
Visual context accelerates identification. Being able to search for specific visual elements—a person in a red jacket, a white delivery truck, movement near an exit—eliminates the guesswork. You're not watching hours of footage hoping to spot something relevant; you're filtering for what matters.
Metadata beats manual scrubbing every time. Systems that automatically tag events—door openings, motion in specific zones, vehicles entering areas—let you navigate to likely incident moments without watching everything in between. If you're investigating theft via a loading dock, you can jump directly to every instance when the dock door opened during your incident window rather than watching continuous footage of a closed door.
The difference between efficient and inefficient security camera footage search isn't just time saved. It's incidents that get resolved versus incidents that remain mysteries because reviewers gave up after hours of unproductive searching.
Isolated video clips rarely tell complete stories. Effective security incident investigations require understanding what happened before, during, and after the main event.
Before the incident: Context matters enormously. An injury in your facility might have been caused by a spill that occurred twenty minutes earlier. A theft might show someone casing your location on previous visits. A dispute might have roots in an earlier interaction. Reviewing footage from 15-30 minutes before the reported incident time often reveals critical context that changes your understanding of what happened.
During the incident: This is what most people focus on—the actual event. But even here, single-camera views can mislead. An incident that appears unprovoked on one camera might show instigation when you review adjacent camera angles. Multiple perspectives matter.
After the incident: What happened after an event can be as important as the event itself. Did someone attempt to clean up evidence? Did parties leave together or separately? Did anyone else discover the scene? This context supports your findings and prevents future disputes about the aftermath.
An incident timeline video that shows this complete sequence is far more valuable than a clip of just the main event. When you present findings to stakeholders—insurance adjusters, legal counsel, HR departments—a clear timeline eliminates questions and accelerates resolution. People can see for themselves what happened, in context, without relying on your interpretation.
Timelines also protect your organization. When everyone can see the full sequence of events, disputes about "what really happened" dissolve. You're presenting evidence, not opinions.
Video footage is your primary evidence, but effective investigations consider multiple dimensions of what happened.
Audio often reveals what video alone cannot. Conversations before an incident, warnings that were given or ignored, sounds that indicate what was happening off-camera—audio provides critical context. For workplace incidents, hearing exactly what was said prevents future disputes about who said what to whom.
Body language and behavior matter enormously. Someone's posture and movements before an incident can show whether they were disoriented, rushed, or deliberately surveilling your facility. The way people react during and after incidents reveals whether events were accidental or intentional. These behavioral cues help you understand not just what happened, but why.
Environment and conditions influence incident interpretation. Was the floor wet? Was lighting adequate? Were visibility obstructions present? Was signage clear? Environmental factors might reveal whether your facility contributed to an incident or whether responsibility lies elsewhere.
Staff interactions and protocols should be reviewed for incidents involving employees. Did staff follow proper procedures? Were safety protocols in place and visible? Did anyone attempt to intervene or assist? This context determines whether incidents reflect individual actions or systemic problems requiring policy changes.
Reviewing context doesn't mean making excuses or shifting blame. It means understanding incidents completely so you can prevent recurrence and respond appropriately. A slip-and-fall incident where your team immediately provided assistance and called for help tells a very different story than one where staff ignored someone in distress—even if the injury itself was identical.
When incidents occur, everyone has a story. Employees have their version. Customers have theirs. Witnesses remember events differently. Without objective evidence, incident investigations devolve into conflicting narratives and "he said, she said" disputes that never reach satisfying conclusions.
Video footage provides a single source of truth that eliminates ambiguity. It shows what actually happened, not what people remember or claim happened. This objectivity is why video evidence for security incidents has become essential for modern business operations.
Insurance claims get resolved faster with video evidence. Adjusters can see exactly what occurred rather than weighing competing statements. Clear footage often means the difference between accepted claims and disputed settlements that drag on for months. When you can show definitively that your facility wasn't at fault—or when you can demonstrate the extent of damage—insurance processes accelerate dramatically.
HR investigations require evidence that protects both your organization and your employees. Workplace disputes, harassment allegations, and policy violations all benefit from objective documentation. Video doesn't replace thorough HR processes, but it provides factual grounding that prevents investigations from becoming exercises in determining credibility rather than establishing facts.
Legal proceedings depend on admissible evidence that can withstand scrutiny. Video evidence for investigations meets this standard when it's complete, unaltered, and properly documented. For liability claims, premise security cases, or criminal proceedings, quality video footage often determines outcomes. Your ability to present clear evidence of what happened—and what security measures were in place—directly impacts legal exposure.
Compliance requirements increasingly expect video documentation. Safety incidents must be reported accurately to regulatory agencies. Access control violations need documentation for audit purposes. Many industries face specific requirements about incident documentation and reporting timelines. Video evidence ensures you can meet these obligations with confidence.
Beyond formal requirements, video evidence serves another crucial function: it prevents incidents from escalating. When all parties can see what actually happened, disputes often resolve themselves. The customer who claimed staff treated them poorly might reconsider their complaint when shown footage of the interaction. The employee who reported harassment can be vindicated by clear documentation. Video doesn't just protect organizations—it protects everyone involved by establishing facts.
Having security camera footage isn't the same as having useful security camera footage evidence. The difference determines whether your video system is an asset during investigations or just a storage expense.
Clarity is non-negotiable. Evidence must be clear enough to identify people, read displays, see conditions, and understand what's happening. Low-resolution footage that shows a blurry figure doing something indistinct isn't evidence—it's ambiguity captured on video. This means your camera infrastructure matters enormously. Cameras positioned too far away, with insufficient lighting, or using outdated sensors produce footage that can't answer the questions you'll need answered.
Continuity matters because gaps in coverage create doubt. If your footage shows someone entering your facility but you can't track them through your space because of blind spots, you haven't documented the incident—you've documented your surveillance gaps. Useful evidence covers the relevant areas completely, without temporal or spatial gaps that allow competing interpretations.
Context transforms raw footage into compelling evidence. A ten-second clip of an incident might technically show what happened, but without context about what preceded it, what followed it, and what was happening in surrounding areas, you're presenting an incomplete picture. Useful video evidence includes enough context that viewers can understand the full situation without having to rely on supplementary explanations.
Accessibility determines whether evidence can actually be used when needed. Footage locked in proprietary systems that require specialized software to view, or stored on local devices that might fail, or accessible only by specific personnel who might not be available—these limitations turn video assets into liabilities. Useful evidence can be accessed quickly by authorized personnel, reviewed on standard devices, and shared with stakeholders without technical barriers.
Shareability extends accessibility to the people who need evidence to make decisions. Insurance adjusters, legal counsel, law enforcement, HR departments, and senior leadership all need to review footage in different contexts. If sharing evidence requires burning DVDs, converting file formats, or sending massive files that can't be opened, your video system is creating friction at exactly the wrong time. Useful evidence can be shared securely and efficiently with everyone who has a legitimate need to review it.
The gap between having cameras and having useful evidence is why many organizations remain vulnerable despite substantial security investments. Footage exists somewhere on your system, but by the time you find it, export it, and share it, the opportunity to respond effectively has passed. Modern approaches to incident investigation with security cameras close this gap by treating video as accessible intelligence rather than buried archives.
The evolution from passive recording to intelligent analysis has transformed what's possible during security incident investigations. Modern video analytics fundamentally change how quickly and accurately you can understand incidents.
Searchable events eliminate the need to watch hours of footage hoping to find relevant moments. Instead of manually scrubbing through timelines, you can search for specific event types: vehicles entering areas, people crossing virtual boundaries, objects appearing or disappearing, doors opening after hours. AI video analytics for security tag these events automatically as they occur, letting you jump directly to moments that matter. For a theft investigation, you can instantly pull up every instance of someone accessing a specific area during your incident window rather than watching days of footage.
Automatic capture means your system identifies and flags unusual activity without human monitoring. Motion in areas that should be empty, people present during restricted hours, vehicles moving through unauthorized zones—these events get captured and tagged even if no one was watching at the time. This automatic awareness is particularly valuable for incidents you don't discover immediately. When you realize inventory is missing but don't know exactly when the theft occurred, intelligent systems can surface likely incidents from days or weeks earlier.
Faster review comes from systems that understand what they're showing you. Rather than presenting undifferentiated video streams, modern platforms highlight relevant activity, summarize patterns, and present evidence in ways that accelerate comprehension. When you're investigating multiple related incidents or trying to identify patterns, analytics compress hours of investigation into minutes of focused review.
Reduced human bias improves investigation accuracy. When reviewers manually search footage, their expectations influence what they notice and what they miss. They focus on likely scenarios and might overlook unexpected explanations. Automated analytics surface all relevant activity impartially, including events that human reviewers might have dismissed or never thought to check. This comprehensiveness prevents incorrect conclusions based on incomplete evidence.
Modern video analytics doesn't replace human judgment—it enhances it. Investigators still make determinations about what happened and what it means. But they make those determinations from complete information, found quickly, rather than from whatever fragments they managed to locate through manual search.
These capabilities also enable proactive security improvement. Patterns in near-miss incidents might reveal safety hazards before someone gets seriously injured. Repeated access violations might indicate policy confusion rather than malicious intent. When analytics surface these patterns, you can address root causes rather than just responding to individual incidents.
Finding relevant footage is only half the challenge. The other half is presenting findings in ways that drive action and support decisions. Effective security incident reporting transforms video evidence into actionable intelligence.
A complete incident report includes several essential elements:
The incident summary describes what happened in clear, factual language without speculation or editorial commentary. This sets context for everyone reviewing the report.
Timeline documentation shows when events occurred, from initial conditions through the incident to aftermath. Precise timestamps let stakeholders verify findings independently.
Video evidence should be embedded or directly linked, showing relevant footage from all pertinent cameras. Include enough context that viewers understand what they're seeing without extensive explanation.
Key observations highlight important details: what actions precipitated the incident, who was involved, what security measures were present or absent, and any environmental factors that contributed.
Supporting documentation might include photos, audio transcripts, witness statements, or related incident reports that provide additional context.
Clear video evidence shortens resolution time dramatically. When stakeholders can see what happened rather than reading descriptions, decisions accelerate. Insurance claims that might have taken weeks get resolved in days. HR investigations reach conclusions without protracted interviews. Legal assessments happen faster because counsel can review evidence directly.
The speed improvement isn't just operational efficiency—it's risk mitigation. Fast incident resolution means:
Clear evidence prevents escalation. Many disputes persist not because parties disagree about what should happen, but because they disagree about what did happen. When video evidence unambiguously shows events, conflicts often resolve themselves. The customer claiming your employee was rude might accept responsibility when shown respectful interaction. The employee disputing a policy violation might acknowledge the violation when shown clear footage.
This de-escalation protects relationships and reduces costs. Customer disputes that might have become legal claims get resolved amicably. Employee grievances that might have required formal proceedings get settled through direct conversation. Incident reporting with video evidence provides the factual foundation that lets all parties move forward constructively.
Modern platforms streamline this reporting process. Rather than manually assembling evidence into reports, systems generate comprehensive incident documentation automatically—complete with relevant footage, timelines, and contextual information. This automation ensures consistency, speeds reporting, and reduces the burden on whoever is responsible for investigation.
The impact of efficient security investigations extends across your entire organization, but specific roles see particularly dramatic improvements.
Operations leaders spend significant time managing incident response and dealing with the operational disruption incidents create. Faster investigations mean faster return to normal operations. When a theft requires reviewing days of footage across multiple locations, operations grind to a halt while someone conducts the investigation. When that same investigation takes minutes, operations continue uninterrupted. Operations teams also benefit from pattern identification—understanding whether incidents reflect isolated events or systemic problems requiring operational changes.
Security teams exist to prevent and respond to incidents, but traditional investigation tools make response painfully slow. Modern approaches to security investigations for businesses let security personnel focus on actual security rather than forensic video review. They can identify threats faster, respond more effectively, and provide better evidence to stakeholders. For enterprise security teams managing multiple facilities, centralized investigation capabilities mean they can oversee incident response across locations without traveling to each site to review local systems.
IT departments inherit responsibility for security infrastructure even when physical security isn't their primary focus. They manage camera systems, troubleshoot access issues, export footage, and convert file formats. Streamlined investigation platforms reduce IT burden by making these systems accessible to the people who actually need them. When operations managers can review footage independently, IT isn't a bottleneck for every incident investigation.
Executives and senior leadership care about security investigations primarily when they represent significant liability, legal exposure, or reputational risk. Fast incident resolution means executives can make informed decisions about response, communication, and risk mitigation while situations are still manageable. When serious incidents occur, leadership needs clear answers quickly to determine next steps. Waiting days for investigation results limits response options.
The business case for faster investigations connects directly to core business concerns:
Risk reduction happens when you can identify and address security vulnerabilities before they become major incidents. Faster investigations mean faster pattern identification and faster remediation of systemic problems.
Cost savings accumulate across multiple dimensions. Less time spent on investigations means lower labor costs. Faster insurance claim resolution means faster reimbursement. Resolved disputes avoid legal expenses. Identified patterns prevent costly incidents before they occur.
Reputation protection depends on how you handle incidents when they inevitably happen. Organizations that investigate thoroughly, respond quickly, and present clear evidence maintain trust with customers, employees, and partners. Organizations that fumble investigations, provide vague explanations, or seem unable to establish facts damage their reputation regardless of what actually happened.
The physical security investigation process shouldn't be where your organization's ability to function effectively breaks down. Modern approaches ensure it becomes a strength—demonstrating operational competence and risk management capability rather than exposing organizational limitations.
Even with good intentions and adequate resources, investigations often produce poor outcomes because of predictable errors. Recognizing these security investigation mistakes helps you avoid them.
Starting with assumptions about what happened rather than following the evidence leads to incomplete investigations. When you believe you know what occurred, you search for confirmation rather than truth. You review limited footage that supports your theory and ignore evidence that contradicts it. The result is confident conclusions based on incomplete information. Better investigations start with questions, not answers, and follow evidence wherever it leads.
Reviewing too narrow a time window misses critical context. Focusing exclusively on the moment when an incident became obvious means you miss precipitating events, earlier interactions, or conditions that contributed. A workplace injury at 3:00 PM might have been caused by a spill at 2:30 PM. A theft might show planning behavior hours earlier. Expanding your review window ensures you capture the full story.
Ignoring context beyond primary footage produces incomplete understanding. An incident that looks straightforward from one camera angle might appear completely different from another perspective. Environmental conditions visible in surrounding areas might explain behavior that seems inexplicable in isolation. Staff present in adjacent areas might have relevant information. Comprehensive investigations review all available evidence, not just the most obvious footage.
Delayed response lets evidence degrade and situations escalate. When investigations don't begin promptly, witness memories fade, systems overwrite footage, parties develop conflicting narratives, and minor disputes become major conflicts. Investigation delays often occur not because people don't want to investigate but because the investigation process is so cumbersome that it gets postponed until someone has time to deal with it. Making investigations fast makes them timely.
Incomplete documentation undermines investigation value even when you reach correct conclusions. If you don't document findings clearly, with supporting evidence and clear timelines, your investigation can't support the decisions it should inform. Insurance won't accept vague summaries. Legal proceedings require documented evidence. HR processes demand clear records. Thorough documentation isn't overhead—it's the deliverable that makes your investigation useful.
Over-reliance on single sources creates vulnerabilities. Investigations that depend entirely on one camera angle, one witness account, or one type of evidence can be challenged effectively. Multiple corroborating sources create confidence in findings and make them defensible if disputed.
Failure to preserve original evidence can invalidate your findings. Once footage is reviewed, it should be preserved in its original format with clear chain of custody. Edited clips, converted formats, or footage that's been enhanced might not be admissible when you need it most. Proper evidence preservation ensures investigation findings remain credible.
Avoiding these mistakes doesn't require expensive tools or specialized training. It requires systematic approaches that treat investigation as a discipline rather than a task someone handles when they have time.
Organizations that have transformed their incident response capabilities share common approaches that distinguish them from peers still struggling with traditional methods.
Centralized video management brings footage from all cameras and locations into unified platforms where authorized personnel can access everything they need from anywhere. Instead of maintaining separate systems for different facilities—each with its own interface, credentials, and export process—modern approaches provide single-pane visibility across entire operations. For multi-location businesses, this centralization is transformative. A regional manager can investigate an incident at any location without traveling to site or requesting that local staff conduct reviews.
Learn how LiveReach centralizes video across all your locations →
Searchable footage changes investigations from hunting expeditions into targeted queries. Rather than manually reviewing hours of video, investigators search for specific events, times, or visual elements and jump directly to relevant moments. This searchability comes from systems that automatically index video as it's captured, creating searchable metadata that makes footage navigable.
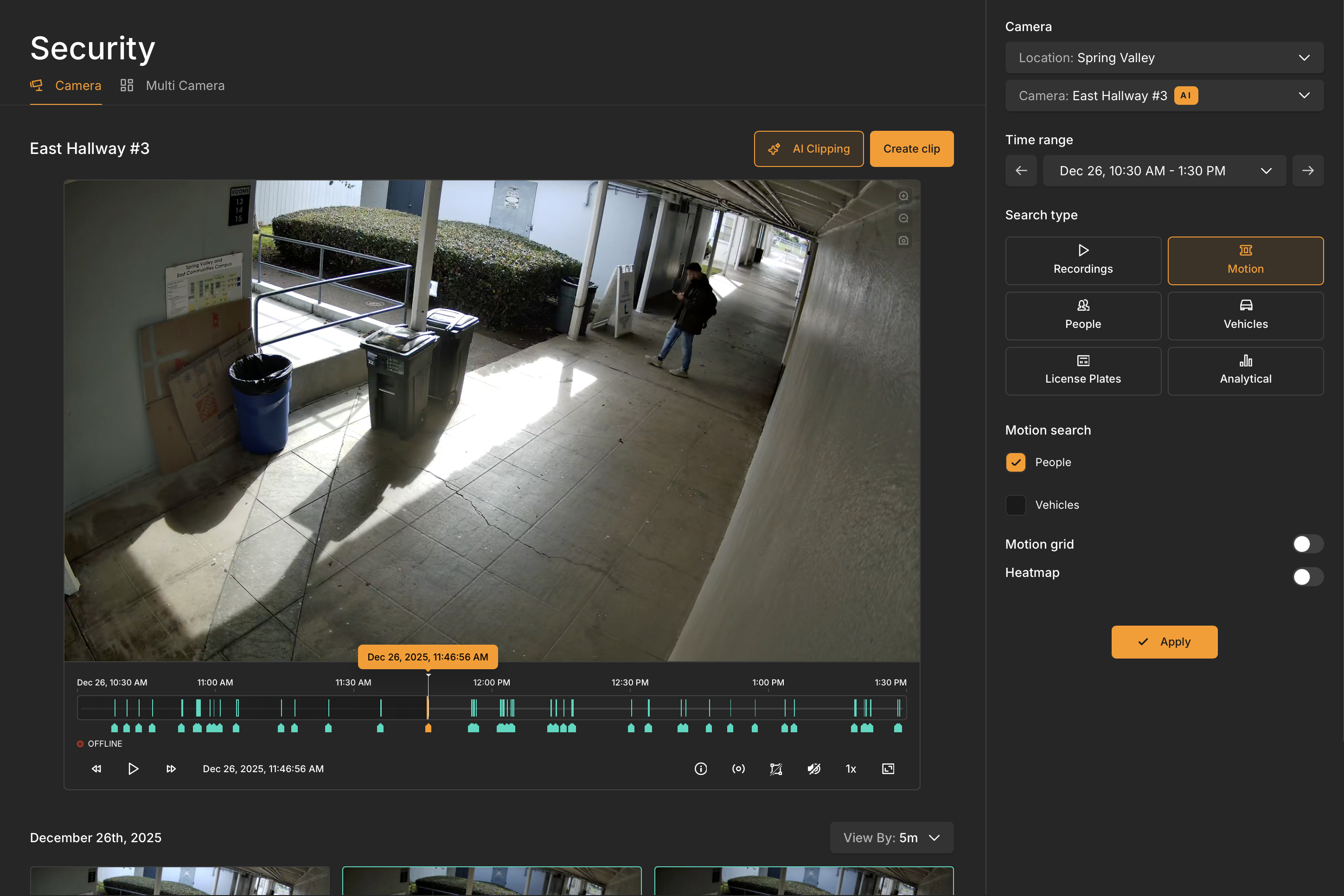
Platforms like LiveReach automatically index every frame of video, tagging objects, people, and events in real-time. This means when an incident occurs, you're not starting from scratch—the footage is already organized and searchable.
The most advanced systems enable natural language search, letting investigators type queries like "person in red shirt near loading dock between 2-4 PM" rather than manually scrubbing through hours of footage. Organizations like San Diego Youth Services have reduced investigation time from hours to minutes using text-based search to find specific moments across their facilities.
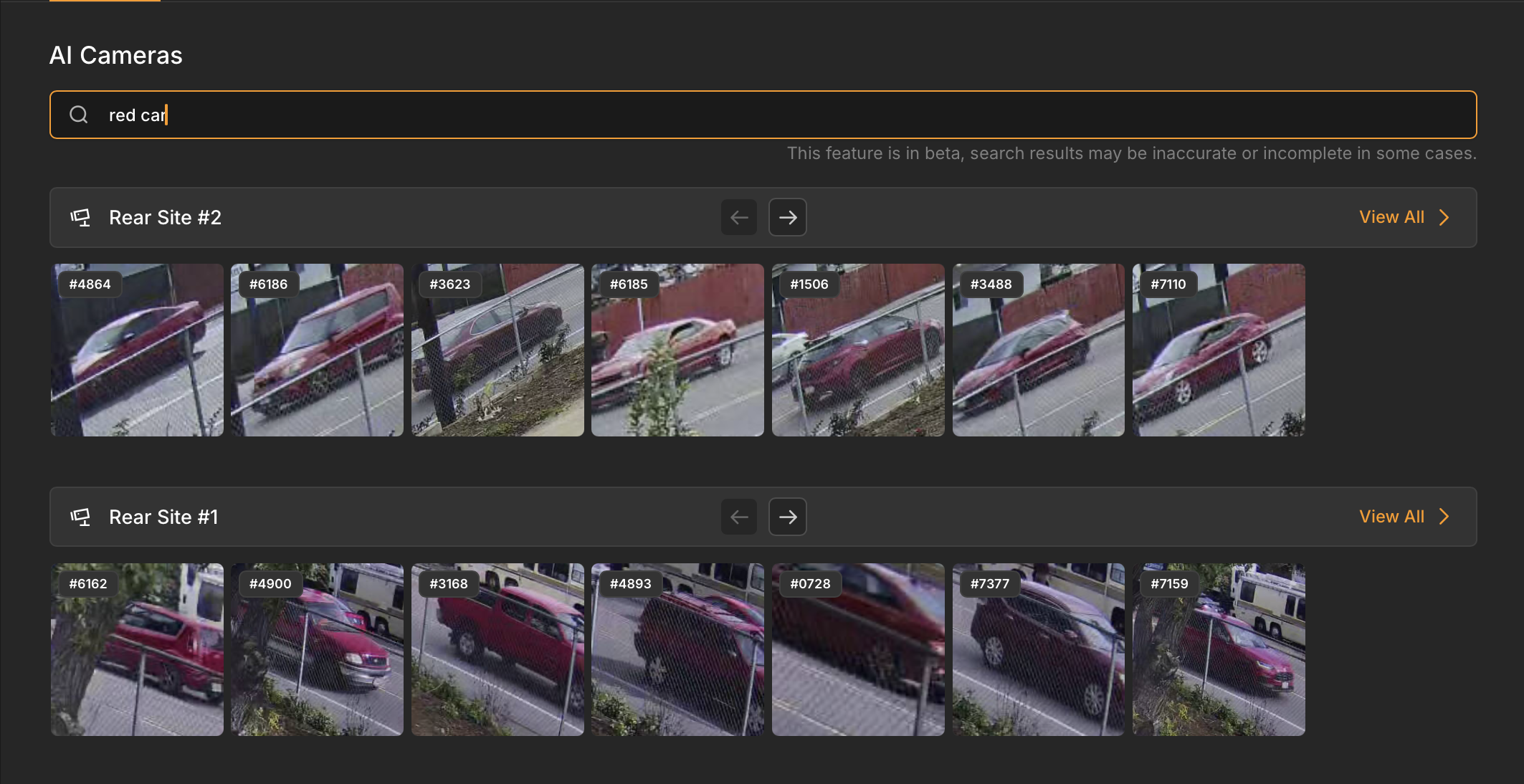
The time savings are substantial—investigations that took hours now take minutes—but the accuracy improvement might be even more valuable. When you can comprehensively search footage, you find evidence that manual reviews would miss.
Integrated workflows connect video systems to the tools organizations already use for incident management, reporting, and communication. When security cameras integrate with incident management platforms, case management systems, or communication tools, investigation becomes part of normal business processes rather than a separate activity requiring specialized knowledge. This integration means more people can participate in investigation and response without becoming video system experts.
See how LiveReach integrates with your existing tools →
Multi-site visibility lets organizations understand patterns across locations that would be invisible when reviewing sites individually. Theft patterns, safety incidents, operational challenges—these often manifest across multiple locations before becoming obvious at any single site. Centralized platforms surface these patterns, enabling proactive response rather than reactive crisis management after problems have become serious.
Organizations implementing these approaches report dramatic improvements in faster security investigations. Investigation time drops from hours or days to minutes. More incidents get fully resolved rather than abandoned as too time-consuming to pursue. Liability exposure decreases because evidence gets preserved and presented effectively. Staff responsible for incident response spend less time on forensic review and more time on actual security or operations.
The shift isn't just operational—it's strategic. Organizations that can investigate incidents quickly and comprehensively demonstrate operational maturity that builds trust with customers, employees, insurers, and regulators. They resolve disputes fairly, prevent incident recurrence through pattern analysis, and protect themselves from liability through clear documentation. These capabilities compound over time, creating increasingly safe and well-managed operations.
Security incident investigations don't fail because businesses lack cameras. They fail because traditional approaches to footage review were never designed for the rapid incident response modern operations require. Organizations accumulate years of recorded video while remaining unable to answer basic questions about what happened last Tuesday.
The investigation process you use determines whether your security infrastructure is an asset or an expense. Traditional manual review processes consume staff time, delay decisions, and often produce incomplete findings. Modern approaches that centralize footage, make it searchable, and integrate it with business workflows transform investigations from multi-day projects into minutes-long queries.
The organizations benefiting most from improved incident investigation capabilities share a common realization: video isn't just surveillance anymore—it's operational intelligence. They use it not just to investigate incidents after they occur but to understand patterns, improve processes, and prevent future problems. This shift from reactive investigation to proactive intelligence represents the future of physical security.
When incidents occur at your facilities, you need answers quickly. Clear timelines. Definitive evidence. Documentation that supports decisions. The difference between organizations that achieve this and those that don't isn't camera coverage—it's clarity about what their systems captured and the ability to surface it instantly.
Learn how modern video intelligence platforms help businesses investigate incidents in minutes rather than days. Explore how LiveReach transforms security footage into searchable, shareable evidence that accelerates response and protects your operations.
Schedule a demo of our platform to see how LiveReach can improve security at your organization.
Request Demo